Fear Is the Mind Killer…

An unusual number of friends and readers have been reaching out to me privately over the past two weeks, all asking the same question: “What can I do to protect my computers from the Russians?”
I understand the fear. I’m also glad that current events are making so many people take their first - or tenth! - look at their digital privacy and security measures. Revisiting your tools, plans, and priorities is always a great idea.
But not because “The Russians are coming”.
Unless you happen to be a high-ranking diplomat, government official, or an aide to one of those people, it’s probably safe to assume that you will not personally be targeted by a Russian (or Chinese or North Korean) cyber attack. The better question to ask is this:
If Russia launches a cyberwar, what are the most likely targets in my country and how would a partially or fully successful attack impact me?
Let’s have a look. First at the digital stuff, then at the analog stuff.
Part I: The Important Question
Are you a target?
The best way to understand the answer to that question is to consider a shortlist of other questions:
Are you someone who is or does something very important? Earlier, I used the example of a diplomat. Other examples might include being a local, state, or national political leader, being famous for your profession or being someone who has easy access to people in power.
If your digital devices or records were hacked, would it put your life in physical danger? What about the lives of other people?
Do you own or manage vast sums of money? This question is important for those who have amassed wealth and for the people they hire to manage their money for them.
Do you work at or have virtual access to any kind of public infrastructure? For example, do you work at any of the large utility companies that provide electricity, gas, or energy to an entire city, region, state, or country?
If you answered yes to one or more of these questions, then Part II of this episode will be important for you to read and act upon.
If you answered no to each of these four questions, then you’re most likely not a target for a coordinated cyberattack by the Russians or any other state-sponsored malicious hacking. Congratulations! Let’s take a nice, deep breath and relax.
Breathing feels nice, doesn’t it?
Now for the powerful reminder: even if you’re not being targeted by the Russians, you should still invest time and effort in your own cyber security. That’s because your savings and possessions — however large or small they may be — are of great value to you. Trust me when I tell you: even if the Russians aren’t interested in you personally, there are plenty of other malicious hackers, scammers, and con artists who are very skilled at helping you part with your hard-earned cash.
Two unfortunate examples:
My relatives lost $50,000 to a digital scam. That amount isn’t enough to show up on the radar for any state-sponsored hackers, but it was more than enough for a smaller operation to run a successful phishing campaign to which my cousins fell prey.
A college friend recently had her identity compromised. She fell for a different kind of scam that saw her giving her social security number, birth date, and bank account numbers over the phone to someone she thought represented a state institution. They did not.
Shit happens and it happens to many of us, including those who aren’t rich, famous, or powerful. So it pays to be digitally prepared.
Part II: How To Harden Your Cyber Security
There are concrete steps that ANYONE can take to help strengthen (or “harden”) their digital security measures. I’ll break down some of my top choices below, including the time commitment you might need.
Start Using Multi-Factor Authentication
Skill Level: Beginner to intermediate
Time to learn: 5-10min
Time to set up: 5-10min per account
Cost: free
I hate being a broken record, but it’s important at a time like this to beat the drum. Multi-Factor Authentication (also called “MFA”) is free, easy to use, and can make the difference between your accounts being easy to hack or nearly impossible to break.
MFA ensures that anyone - including you - who tries to access your protected account would require physical access to your cellphone to be able to gain entry. That means even if your username/password are somehow obtained, your MFA-protected accounts will remain safe.
It does this by providing a 6-digit password on your phone that changes every 30 seconds. An MFA-enabled account will ask for this 6-digit challenge code after you’ve logged in with your username and password.
I did a deep dive into MFA in Episode #36 and if you’ve got 5-10min, I recommend that you read to that episode. I think it’s an invaluable tool that I continue to use myself.
I still use the Authy app by Twilio to manage all of my MFA accounts and it’s stood the test of time. You should use it as well. Authy isn’t only just a great app (it is), but the Authy website is also an AWESOME resource on how to set up MFA on many of the world’s most popular platforms. Just use Authy’s easy-to-read guides.
My recommendation: lock every crucial account with MFA that you can. I use MFA to harden my email accounts, my social media accounts, my zoom account, and many of my online payment providers. This includes my bank. You should too.
Some of you may rightly ask: “Um, won’t my needing to produce a 6-digit number as a second challenge mean I’ll have to spend extra time logging into my crucial accounts?” Yes, that’s true. It will cost you another 5-10seconds on each login.
But those extra 5-10 seconds will absolutely help secure your accounts in a huge way. So it’s a huge payoff for the investment.
Please note: If your bank doesn’t provide MFA and you’re someone who really needs to protect themselves… I’d find another bank. I realize that’s a strong statement, but given how easy it is for any institution to set up MFA and given how much MORE secure it is than “security questions”, I don’t understand why it’s not law for all banks to provide this.
Start Using An Open-Source Password Manager
Skill Level: Beginner
Time to learn: 5-10min
Time to set up: 5min to start, 30-60min if you’re migrating from another service
Cost: free
My regular readers know that I use and highly recommend BitWarden as your password manager. Not only is it free but it’s 100% open-source, the gold standard for ANY piece of software. Does that make it better than, say, 1Password or LastPass?
Ummmm, YES. Yes, it does!
I’ve used both 1Password and LastPass: they’re really good and graphically pleasing. But I don’t want a company that will not share their software code with the world to ask me to “just trust” them. Sorry: that’s not how this works. Security and privacy are based on trust. There is no trust unless other people can see and vet your code. That’s what the term “open-source” means.
Also, BitWarden is FREE. LastPass is currently $36/year for a single user. 1Password is too. I’d rather save money and get a better product.
Switching from LastPass? BitWarden’s got a help page for that. Ditto for 1Password.
More importantly, having a password manager means you need to know how to use it. Most people - by a huge margin - use the same password (or passwords that are similar) for all of their crucial websites. You should never, never, never do that.
Never.
Instead, have BitWarden auto-generate a long, complex, and unique password for each and every website you visit. Here’s how:
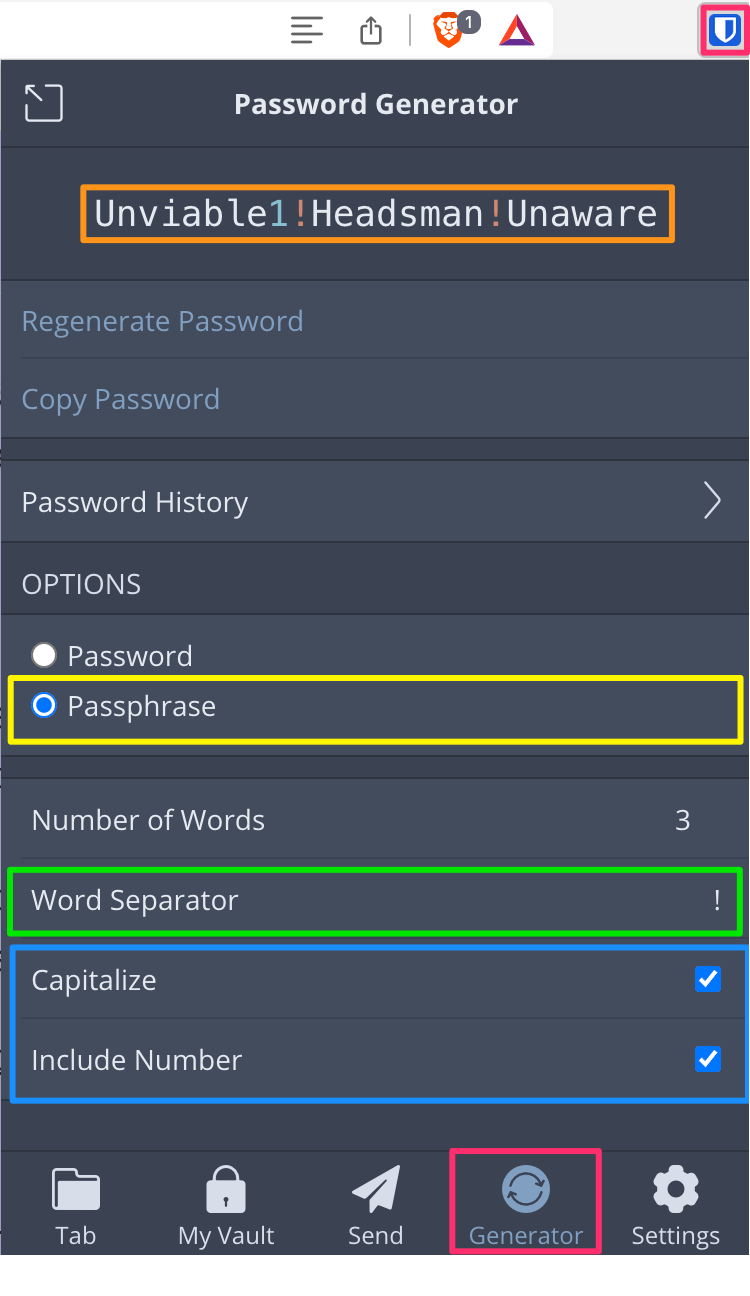
After installing BitWarden and setting up a username and password, click the extension icon in your browser (pink box at top right), then on the “Generator” button (red box at bottom).
When the interface comes up, check the boxes for Capitalize and Include Number (blue box), and check the “Passphrase” radio button (yellow bow). I choose to use an exclamation mark “!” as my word separator (green box) as it’s considered a special character, and I default to at least 3 words as the number of words that will be used.
That part I forgot to put in a tidy, colorful box, but I’m sure you can still find it in the image above, yeh?
BitWarden automatically generates a new password for you with these criteria. In this case, my password is “Unviable1!Headsman!Unaware” which is a fabulous password because it’s both long and complex.
Now, you’ll just want to run this same process for EACH of your various, crucial websites. Should you do this with ALL of your websites. Well, yes. Is that a realistic goal right now? Well, maybe not. So…
Start by using BitWarden to create unique, long, and complex passwords for these kinds of accounts:
email & communications
all social media
banking & financial
any domain registrars that host your websites (GoDaddy, Network Solutions, BlueHost, etc.)
Your password manager!
Set aside 60-90min to start this process and give yourself extra protection from malicious hackers who will most certainly use one of your passwords to open up and unlock other accounts that you keep.
Use a Secure Messaging Platform
Skill Level: Beginner
Time to learn: 10-15min
Time to set up: 5min to start, 10min to add friends/family/colleagues
Cost: free
For messages that require top security and privacy, use a trusted and open-source application that provides end-to-end encryption or E2EE. Currently, there are only two options to consider: Signal and Wire. I discussed both of these messaging services in Episode #39 here and it’s worth investing 10-15min of your time to give that a read.
I personally use Signal for anything I need to communicate that I consider important: sharing a password, discussing a private medical matter with a friend, or chatting with any of my family’s legal or financial team.
While Apple has claimed to be a champion of privacy, they’ve caved to demands from both Russia and China for those regimes to be able to access user data, so I can’t trust them in this department.
Facebook owns WhatsApp, so they, too, cannot be trusted.
Signal and Wire it is.
For email, the gold standard in secure messaging is ProtonMail. The company offers both free and paid tiers with different perks and benefits. I’ve used the free tier for many years without a problem. ProtonMail deserves the accolades and positive reviews they regularly receive.
Stop Allowing Others To Track Your Whereabouts
Skill Level: Beginner
Time to learn: 0min
Time to set up: 0min
Cost: free (minus the cost of having a smartphone)
Some of you will read that section title and think I’m talking about posting your whereabouts on social media or giving others access to your whereabouts using Apple’s FindMe feature.
I’m not… (although you really should stop doing those two things).
I’m talking about your actual smartphone itself: the electrical transmitter and receiver that uses Bluetooth, WiFi, cellular data, and GPS coordinates to help identify where you are… and that you usually keep in your pocket.
Practically speaking, high-target individuals and their teams don’t really have a choice here: if you don’t want to be tracked by others, then you need to leave your phones at home when you travel.
“But David!” you scream, “It’s my phone! I need it!”
Do you? Do you REALLY need your phone every time you go out? Because there was a time not too long ago when none of us had smartphones and we all seemed to navigate through our lives just fine. If we needed to meet someone, we called them in advance and agreed on a time and place.
“But, David!” you scream again, “I can just put my smartphone in airplane mode, and then I can’t be tracked.”
Actually, no: your phone still tracks your location when it’s in airplane mode.
Wanna blow your mind? Open up your smartphone maps application. Put your phone into airplane mode. Now, get in a car or taxi and watch what happens on the map as you’re moving.
The map tracks your location. Still. While you’re in airplane mode. Here’s a video from my own phone that I shot yesterday.
If you believe you’re a high-visibility target for hacking and you must travel with your phone, please read Episode #8. There, I walk my readers through how to set up and then use a more secured mobile device.
Part III: What’s More Likely To Happen
If you want to know what the Russians might do, then you need to think like a dictator who wants to disrupt and then punish his adversaries into submission.
Russia has an established track record of seeking to compromise and inflict chaos on its enemies, even before a single shot is fired. In the US (and in other countries) that’s been accomplished both via relentless social media disinformation campaigns and through notable and malicious hacks like the Solar Winds attack which, in 2020, breached servers throughout the US Government.
This is why I’d expect more of the same should the Russians start a more direct cyberwar with the US. In this scenario, targeting a handful of individuals won’t disrupt the enemy: to do that, you need to go for the jugular. For most developed nations, that’s public infrastructure, how we all get our electricity, water, and gas.
And, hot news flash: Russia’s already started that campaign. In case you’ve not been paying attention, they started YEARS ago.
In 2018, then-Secretary of Energy Rick Perry spoke to Congress and said that cyber attacks on American infrastructure were “literally happening hundreds of thousands of times a day.”
Last year, in 2021, a hacking collective known as “Dark Side” breached the Colonial Pipeline, an oil refinery that pumps 2.5 million barrels of oil a day here in the US. The group is thought to be Russian in origin.
The Best Solution: Prepare
When I lived in Los Angeles, we all learned to keep prepared for the eventuality of an earthquake. This meant stocking up some food, blankets, candles, pet supplies & and any crucial medications. Also, some hard-toe shoes to be able to walk over the glass that might have shattered. Then, when earthquakes struck - and I lived in LA during the Northridge quake of 1992 - many of us were far better prepared to live without everyday luxuries like electricity and/or gas for some periods of time.
This is no different.
If and when Russia strikes, I assume they’ll go after utility companies and find ways to shut down the flow of oil, gas, electricity, and water. Millions can be impacted. More chaos is possible. But not if people prepare.
So go analog, friends. Have a 5-10 day reserve of:
food
fuel
drinking water
warmth or cool depending on your environment
light or back-up power, like a generator
any supplies you need to care for your pets, elderly relatives, etc.
Being prepared is a proven technique. It not only works if you live in areas where there are natural disasters like earthquakes, hurricanes, and tornados, but it also works when dealing with the prospect of war. More importantly, preparing feels good: it’s an insurance policy you’ll be so glad you’ve got should the day ever come when you need it.
And that’s a wrap for today’s episode, everyone. Thanks again to my free and paid subscribers for supporting independent technology journalism. I also thank you, in advance, for using the link below to share Tech Talk with your friends, family, and colleagues.
As always… Surf safe.
Popular Past Issues:
Which secure routers to purchase and WHY.
My 2021 recommendations on the best VPN providers.
My favorite, free tool to keep email addresses private.
A crash course on keeping your devices updated.
Product Recommendations
These are the devices and services that I personally use. I pay for everything you see listed here. I made these choices after much research and recommendations from tech industry colleagues.
The online backup software I use: iDrive (affiliate link)
The VPN software that I use: Nord VPN (affiliate link)
The email anonymizer that I use: 33Mail (affiliate link)
The secure router I use at my office: Gryphon (affiliate link)
The secure router I use at my home: Synology (affiliate link)
The service I use to block spam calls/texts: Uncall (affiliate link)
Transparency Statement
Some of the products and services I recommend pay me a small commission if you decide to purchase them. Making purchases based on my recommendations never costs you extra. In fact, it can sometimes save you money because I get access to certain discounts which aren’t available to the general public.
It’s a win-win: you save money and help me earn an additional salary from my writing. Thank you, in advance, for that. It’s an easy way for anyone to support my work, research, and expertise. Affiliate links will be shown like this → (affiliate link) to make them easy to identify.
In case you’re curious:
I’ve purchased, owned, tested, and/or deeply researched every single thing I recommend.
I’m never paid to sell software or hardware to you.
I retain 100% editorial control over everything I write.
The companies, products, or services that I recommend don’t know that I’m going to mention them.
















Episode #55: The Russian Threat